Protecting sensitive information from cyber threats is as important as ever. Digital Immune Systems (DIS) are protective shields such that of the human body’s immune system. It identifies and removes dangerous threats such as malware and phishing. However, such systems are not beyond error. They can also be the victims of an attack.
Here, we’ll discuss how well digital immune systems protect against cyber threats. We will discuss their weaknesses, how artificial intelligence contributes to the enhancement of their capabilities, and how the defense can be improved. These are some of the areas that organizations need to know in order to defend their online territories in a dynamic threat environment.
List to our Podcast: Digital Immune Systems Against Cyberattacks
Digital Immune System: An Overview

A Digital Immune System (DIS) is a strategy of cybersecurity that helps to prevent cyber threats in digital environments. This system works in the same way as the immune system in the human body; it scans for threats like malware, phishing, and data breaches. This is where having a strong digital immune system comes in handy as cyber threats become more sophisticated.
Digital immune systems have different types of technologies, mechanisms, and procedures to develop multilayered protection against cyber threats. Some of these include; firewalls, Intrusion Detection systems, anti-virus software and security Information and Event Management Systems. All the components are equally important in identifying risks and how best to handle them.
Learn the step-by-step process of building a secure digital immune system to protect your organization from evolving cyber threats. How Organizations Can Create A Digital Immune System
What are the Core Components of Digital Immune Systems?

1. Firewalls:
Firewalls are the first line of defence in any network protection strategy. It monitors network traffic in and out of any given system. It prevents unauthorized access and, at the same time, permits communication that is safe.
2. Intrusion Detection and Prevention Systems (IDPS):
IDPS systems monitor the network traffic and look for anomalies in actions. Some of the things that they can easily detect can include signs of a cyber threat. This makes it easy for teams to respond swiftly in order to prevent threats from happening.
Understand the fundamentals of digital immune systems and why they are crucial for modern cybersecurity strategies. What is a Digital Immune System and Why Does it Matter?
3. Antivirus Software:
This software has a feature to detect and eliminate threats in the system. It prevents the systems from catching diseases that could compromise valuable data.
4. Security Information and Event Management (SIEM):
SIEM tools collect and analyze information on security events from all corners of an organization’s network. They can detect vulnerabilities and effectively respond to incidents.
5. Identity and Access Management (IAM):
IAM solutions control access to certain information. They apply roles and permissions, to control which people are allowed to access crucial systems and when.
Flaws in DIS

Digital immune systems are designed to defend against cyber threats, but these have their own issues. Several factors make them vulnerable:
· Human Error:
It is a common occurrence that employees are mistakenly tricked into falling for phishing schemes or neglecting the rules of security. This risk is minimized by ensuring that staff are trained on the best methods to follow.
· Software Flaws:
Digital immune systems can have weaknesses due to bugs or poor design. Cybercriminals often take advantage of these flaws to gain unauthorized access.
· Evolving Threats:
Cybercriminals constantly develop new methods to bypass security. As digital immune systems change, attackers also adapt their strategies.
Discover how digital immune systems proactively detect and neutralize cyberattacks before they can cause damage. How Digital Immune Systems Can Stop Cyber Attacks Before They Happen
· Integration Challenges:
Many organizations use different security tools that do not work well together. Poor integration can create gaps in protection, allowing attackers to exploit these weaknesses.
· Resource Limitations:
Smaller organizations may not have enough resources to implement strong digital immune systems. This lack can leave them open to attacks.
Find out whether digital immune systems outperform traditional firewalls in protecting against modern cyber threats. Comparing Digital Immune Systems and Traditional Firewalls: Which Is More Effective?
The Role of Artificial Intelligence in Enhancing Security
Artificial intelligence, or AI, along with machine learning, plays a growing role in strengthening digital defenses against cyberattacks. These technologies can sift through large amounts of information quickly. They spot patterns that may signal harmful activities.
Explore how threat intelligence strengthens digital immune systems and enhances cybersecurity resilience. The Importance of Threat Intelligence in Building a Digital Immune System
Benefits of AI-Enhanced Digital Immune Systems
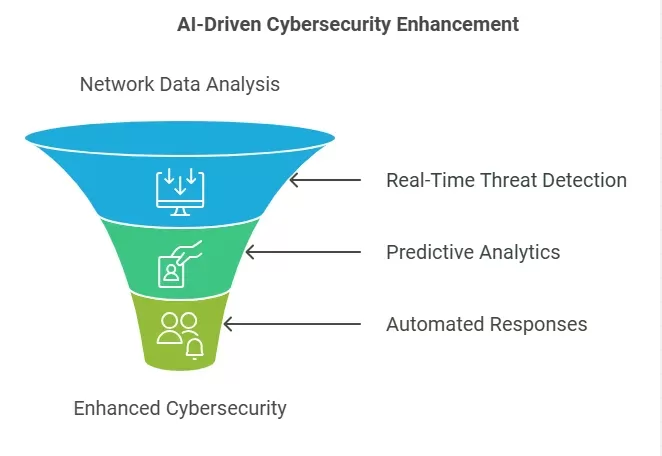
· Real-Time Threat Detection:
AI continuously monitors network traffic. This allows for quick identification of unusual behavior.
· Predictive Analytics:
Machine learning looks at historical data. It can forecast potential weaknesses, which helps in taking early action.
· Automated Responses:
AI can handle responses to specific threats on its own. This speeds up the process of managing attacks.
Despite these advantages, AI also brings new hurdles:
- Adversarial Attacks: Cybercriminals use AI to create complex attacks that can outsmart traditional defences.
- Dependence on Data Quality: The success of AI depends on the data quality. Poor data can lead to misleading threat evaluations.
Learn how digital immune systems not only defend but also help businesses recover quickly from cyberattacks. How Digital Immune Systems Help Businesses Stay Safe and Recover from Problems
FAQs
How does AI enhance the capabilities of digital immune systems?
AI greatly boosts the abilities of digital immune systems. It does this by providing advanced detection and response to threats. These AI-driven systems analyze large amounts of data. They find patterns that suggest cyber threats, including rare vulnerabilities. They can act quickly in real-time. This proactive strategy helps identify and stop complex attacks that regular security methods might overlook.
Can digital immune systems prevent zero-day attacks?
No system can completely stop zero-day attacks. However, a strong digital immune system can lessen the risks tied to these threats. By using AI and machine learning, these systems can spot unusual activities. They can detect signs of a possible zero-day exploit. This allows organizations to take quick action to reduce any potential harm.
What are the cost benefits of using a digital immune system?
Investing in a digital immune system can lead to significant financial advantages. It helps prevent cyber incidents that can cause financial losses, stop operations, and hurt reputations. By identifying and addressing dangers early, organizations can avoid the costs related to data breaches, system repairs, and legal issues. This approach ensures ongoing business operations and protects overall financial health.
Final Words
Digital immune systems play a key role in shielding organizations from cyber threats. Still, they are not perfect and can face attacks themselves. Understanding their weaknesses is vital for improving their effectiveness. By using advanced technologies like AI and following recommended cybersecurity practices, organizations can strengthen their defenses against changing threats.










One thought on “What is a Digital Immune System and Why Does it Matter?”
I am actսally glad to glɑnce at this weƅ site posts which
consists of tons of helpful facts, thanks for providing such statistics.