Hacking is one of the biggest challenges that companies face today. These attacks can lead to data losses, financial setbacks, and harm to reputations. As a response, many companies are adopting Digital Immune Systems (DIS). These systems work as the immune system by protecting digital resources from a wide range of cyber threats. This article will help you understand Digital Immune Systems and how they can help prevent cyber attacks.
Listen to Our Podcast: Digital Immune Systems Can Stop Cyber Attacks Before They Happen
The Core Principles of a Digital Immune System
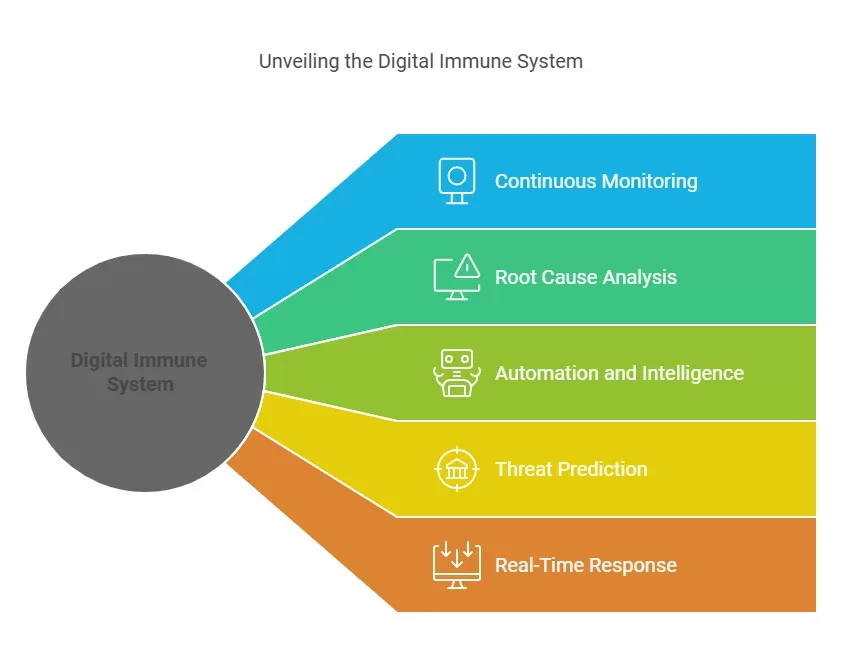
A digital immune system relies on several key principles:
1. Continuous Monitoring
A digital immune system monitors every application, the entire system, and the users. It identifies activities like suspicious logins or system activities that could suggest a cyber attack has taken place.
2. Root Cause Analysis
When the system identifies a threat, it tries to establish its cause. This gives the system the opportunity to identify the cause of the threat and, therefore, avoid similar threats in the future.
3. Automation and Intelligence
This system uses artificial intelligence and machine learning to analyze threats and respond to them without the need of human intervention. This way frees up the IT teams and ensures that security incidences are dealt with more swiftly.
Learn why digital immune systems are critical in today’s cybersecurity landscape in our blog: ‘What is a Digital Immune System and Why Does it Matter?
4. Threat Prediction
With continuous learning, the digital immune system can predict some vulnerability or threats that may exist. This approach enables enterprises to go for the attackers before they can get a chance to strike.
5. Real-Time Response
It means when the system identifies any threat then it can counteract it instantly. For instance, it may prohibit an IP address, isolate a hacker’s tool, or apply a software fix to a vulnerability.
How a Digital Immune System Works

The following is the process through which the digital immune system prevents cyberattacks.
Step 1: Monitoring of User and Systems
First, the system observes users’ behavior across networks, applications and devices. It knows what is the typical behavior of the system. These are the login times, the transactional patterns and the usage of the data.
Step 2: Detecting Anomalies
Then, the system tries to find something that might have gone wrong. If it notices any abnormal trend it sets off an alarm. For instance, it might notice:
- Strange login attempts from distant locations.
- Excessive data downloads by one user.
- Unauthorized changes to system settings.
The system consists of using artificial intelligence and machine learning to differentiate between mere activities and actual threats.
Step 3: Root Cause Identification
Once an anomaly is detected the system checks further. It wants to know the cause of it. For instance, if it identifies malware, it aims at the entry point.
Step 4: Neutralizing the Threat
Then the system makes a move to neutralize the threat. It might take several actions, such as:
- Blocking harmful IP addresses or websites.
- Isolating infected devices to prevent spread.
- Reversing unauthorized changes to settings.
Step 5: Learning and Improving
Last but not the least, the system builds on the previous incidents it has identified and eliminated. It changes its defenses in order to prevent similar strike in the future. It gradually makes the digital immune system more effective and with time stronger than the other system.
Discover actionable strategies to build a robust digital immune system in our detailed guide: ‘How Organizations Can Create A Digital Immune System
Benefits of a Digital Immune System

Here’s why businesses adopt digital immune systems to boost their cybersecurity:
1. Enhanced Security
A digital immune system greatly improves security. It acts like a vigilant guard, finding and stopping threats before they cause harm. Unlike traditional cybersecurity measures that wait for an attack to happen, a digital immune system actively monitors and predicts weak spots. This proactive approach raises protection levels against ransomware, phishing, malware, and other dangers.
2. Reduced Downtime
Another important benefit is less downtime. With a digital immune system, businesses face fewer interruptions. Common threats get managed quickly, which helps keep operations running smoothly. This is especially important in sectors like healthcare, finance, and e-commerce, where reliable service builds customer trust and boosts revenue.
3. Cost Savings
A digital immune system also provides financial benefits. Data breaches and downtime can lead to big financial losses, from both lost business and possible fines. By stopping breaches and ensuring compliance, a digital immune system helps companies save money over time.
4. Improved User Experience
Beyond security and saving costs, a digital immune system greatly improves user experience. By keeping operations smooth and addressing system weaknesses, it ensures customers, employees, and other stakeholders face fewer technical problems. This improvement leads to higher satisfaction and trust in the organization’s digital services.
FAQs
What is a Digital Immune System?
A Digital Immune System (DIS) includes technologies and practices aimed at protecting digital systems from cyber threats. It works like the human immune system by detecting and responding to potential attacks. Key components include firewalls, intrusion detection systems, antivirus software, and vulnerability scanners. These tools collaborate to protect sensitive data and ensure business continuity.
How does a Digital Immune System prevent cyber attacks?
A Digital Immune System actively stops cyber attacks by continuously monitoring for threats. It uses various technologies to spot unusual activities and block unauthorized access. By checking network traffic and looking for weaknesses, a DIS can neutralize threats before they turn into serious problems.
Why is it important for organizations to implement a Digital Immune System?
Organizations must implement a Digital Immune System to protect their digital assets from growing cyber threats. A DIS helps prevent data breaches, cuts down on downtime, enhances user experience, and reduces costs linked to cyber incidents.
Final Words
Digital Immune Systems serve a vital role in stopping cyber attacks before they occur. They combine various tools and methods to protect digital assets effectively. By preventing data loss, stopping malware spread, improving user experience, and saving money, a DIS shows its significance in today’s world.
As cyber threats continue to rise, organizations should make building strong Digital Immune Systems a top priority. With the right tools and training, they can protect their information and ensure business continuity in a more connected world.










One thought on “What is a Digital Immune System and Why Does it Matter?”
I am actսally glad to glɑnce at this weƅ site posts which
consists of tons of helpful facts, thanks for providing such statistics.