Phishing and social engineering are two techniques employed by those carrying out cybercrimes. They employ these tricks with the aim of robbing the concerned individuals of their identity or of their money. Social engineering is cantered on psychological tactics of controlling people. It is basically founded on factors such as trust and fear. Phishing is a form of end-user security threats different from hacking and usually takes place in emails.
Each of the methods carries risks and, if applied, can cause a range of issues to the individuals and businesses in question. Knowledge of these is useful in ensuring that people do not fall victim to the tricks these wicked individuals perpetrate on the internet.
Listen to Our Podcast: Social Engineering vs Phishing
What are Key Differences Between Social Engineering and Phishing
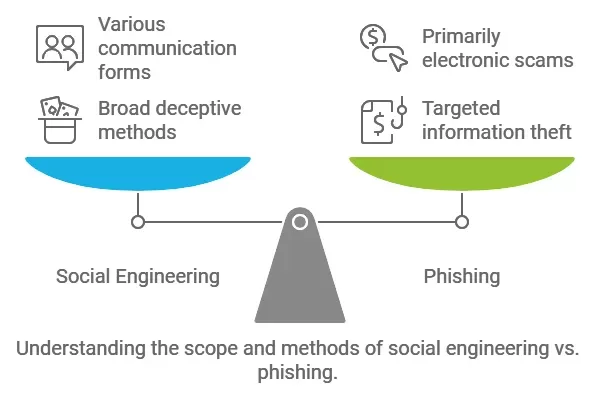
It becomes important to differentiate between social engineering and phishing if one is to avoid the threat that comes with it. Although both involve an act of tricking someone into giving out some information, the two are not similar in their scope and method.
Definitions
1. Social Engineering:
This is a general term that relates to different methods that are employed in a way that will compel people to reveal secrets. It can include impersonating, teasing, or attempting to deceive, pretexting, or something else. Social engineering can be done on the internet, through email or face-to-face interaction.
Curious about how social engineering tactics manipulate human behavior? Discover the techniques used by cybercriminals in our detailed guide! What is Social Engineering and How Does It Work?
2. Phishing:

Phishing actually falls under the category of social engineering. This is typically experienced via emails or messages that may seem like they have been sent from familiar parties. The purpose of common scams is to extract certain information from the target, for example a password or a credit card number.
Methods Used
Social Engineering Techniques:
- Impersonation: The attacker presents himself as a close friend or a family member of the victim.
- Baiting: The attacker comes at the victim with something that may be considered as a gift or an opportunity.
- Pretexting: The attacker devises a fake situation with an aim of eliciting information.
Phishing Techniques:
- Email Phishing: Employing e-mail spoofing and other types of phishing to get target victims to send money or personal identifiable information.
- Spear Phishing: Sending specific messages to specific people.
- Vishing: Conning victims through phone calls with intention of obtaining some information from them.
Want to understand the impact of social engineering on your organization’s security? Read our article on social engineering and its role in cybersecurity
Goals
Social Engineering Goals:
- As a form of social engineering to get people to reveal information on some systems or other important information.
- To take advantage of human feelings such as trust and fear.
Phishing Goals:
- To directly acquire personal data through deceptive mails.
- Instead, used fake links that when clicked, would allow him to install malware on the victims’ devices.
Common Targets
Social Engineering Targets:
- Individuals in various settings, including workplaces and public spaces.
- Organizations where attackers can exploit employee trust.
Phishing Targets:
- Anyone with an email address, especially those who may be less tech-savvy.
- Specific organizations, particularly financial institutions and large companies.
How the Six Principles of Influence by Robert Cialdini Apply to Phishing Attacks

Robert Cialdini’s six principles of influence that are reciprocity, commitment and consistency, social proof, authority, liking, and scarcity. They play a significant role in how phishing attacks are crafted and executed.
Cybercriminals exploit these psychological triggers to manipulate victims into taking actions that compromise their security. Understanding these principles can help individuals recognize and resist phishing attempts.
1. Reciprocity
The principle of reciprocity suggests that people feel obligated to return favors. Phishing attacks often use this principle by offering something enticing at the beginning of the interaction. For example, an email might promise a reward or a free service in exchange for personal information.
When victims perceive they are receiving something valuable, they may feel compelled to reciprocate by providing their details.
2. Commitment and Consistency
Once someone commits to a statement or action, they are more likely to follow through, even if it no longer makes sense. Phishing emails may ask recipients to confirm their account details or agree to terms that seem harmless at first.
Once individuals commit to this action, they may feel pressured to comply with further requests, such as clicking on malicious links or downloading attachments.
3. Social Proof
People tend to look to others for guidance on how to behave. Phishing attacks often exploit social proof by including references to how many other users have taken action. For instance, an email might claim that “thousands of customers have already verified their accounts.”
This tactic creates a sense of urgency and encourages victims to follow suit without questioning the legitimacy of the request.
4. Authority
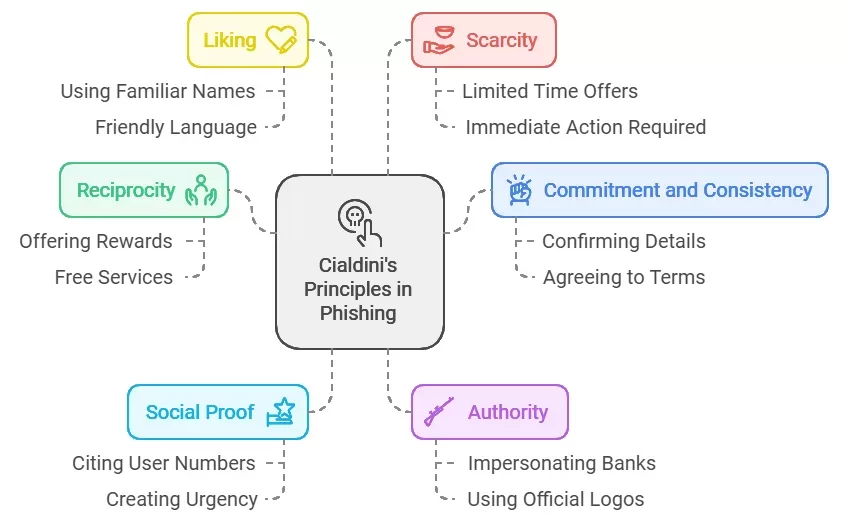
The authority principle states that individuals are more likely to comply with requests from perceived authority figures. Phishing emails frequently impersonate trusted organizations, such as banks or government agencies.
By using official logos and language, attackers create a false sense of credibility that can lead victims to act quickly without verifying the source.
5. Liking
People are more easily persuaded by those they like or find attractive. Phishing schemes may use familiar names or friendly language to create a sense of trust.
For instance, if an attacker hacks an individual’s email account and sends messages to their contacts, those recipients may be more likely to respond positively because they recognize the sender.
6. Scarcity
The scarcity principle suggests that people desire things that are perceive as limited in availability. Phishing emails often create a sense of urgency by claiming that offers are only available for a short time or that immediate action is require to avoid negative consequences (e.g., account suspension). This pressure can lead victims to act quickly without careful consideration.
Final Words
Social engineering and phishing are serious threats in our digital world. Both rely on tricking people into giving away important information. Getting to understand these tactics is key to staying safe online. People should learn how to spot suspicious messages. Organizations must train their employees to recognize these attacks. By being aware and cautious, we can protect ourselves from falling victim to these scams.