Did you know? In 2024, there are an average of 2,200 cyber attacks per day, or one every 39 seconds. In the second quarter of 2024, the average number of cyber attacks per organization per week was 1,636, a 30% increase from the previous year. However, these threats are dangerous and businesses require a robust shield to overcome such threats. This is where threat intelligence comes in as an important part of this defense.
This intelligence operates like a digital immune system. In this article, you will learn the most effective ways of incorporating threat intelligence into your security functions. You can develop an active and effective protection against possible cyber threats.
Listen to Our Podcast: Importance of Threat Intelligence in Building a Digital Immune System
Threat Intelligence: An Overview

Threat intelligence is a process of collecting and processing information about possible threats in cyberspace. This entails details on the attackers, the strategies they employ, and the weaponry they use. By knowing this, companies can learn how to stop these attacks from happening in the first place.
Learn how a robust digital immune system can detect and stop threats before they escalate. See how digital immune systems prevent cyber attacks.
Key Parts of Threat Intelligence
- Strategic Intelligence: This gives a general picture of the threat aspect.
- Tactical Intelligence: This focuses on the certain techniques that attackers employ.
- Operational Intelligence: This features aspect of planned attacks.
- Technical Intelligence: This is based on certain IP addresses or viruses for instance.
What is a Digital Immune System?
DIS is a complex of tools and methods that can be used for the protection of digital areas. Similar to the human immune system it is designed to react and protect. It is to search and destroy threats. The key objective is to make it possible to maintain the continuity of digital business operations during an attack.
Main parts of a digital immune system
- Threat Detection: This identifies dangers in real time.
- Response Mechanisms: These act quickly to stop or reduce the impact of threats.
- Recovery Processes: These restore normal operations after an attack.
- Learning Capabilities: This improves defense by learning from past events.
Understand the concept and importance of a digital immune system in modern cybersecurity strategies. Explore what a digital immune system is and why it matters
How Threat Intelligence Strengthens the Digital Immune System
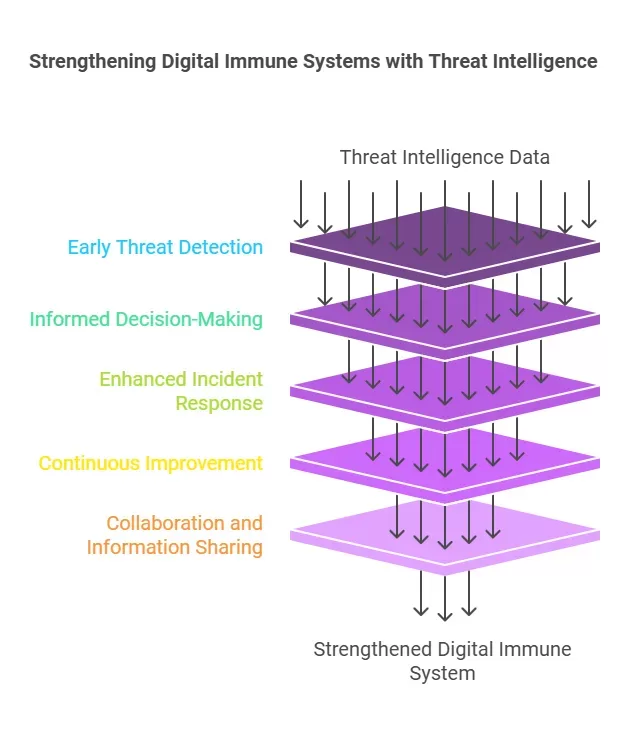
Here’s how threat intelligence strengthens the DIS:
1. Early Threat Detection
Another important benefit of threat intelligence is prevention of potential threats. There are many sources that organizations can watch for indications of compromise, or IOCs. It assists them in identifying attempts at malicious operations before they escalate into major security threats. Measures like these ensure there is prompt action since threatening events are early detected and so less damage occurs.
2. Informed Decision-Making
Threat Intelligence is the information that organizations require to understand the tactics, techniques, and procedures of cyber threats. This information enables security personnel to take right actions, understand the risks and threats, and hence control the resources used in security.
3. Enhanced Incident Response
In the case of a breach, threat intelligence helps organizations know how to act appropriately. Understanding the threat and the approach of attackers allows security teams to develop specific countermeasures. This approach makes it possible to minimize the time and the consequences of security incidents.
Compare the efficiency of digital immune systems with traditional firewalls in tackling modern cyber threats. Find out which cybersecurity method is more effective
4. Continuous Improvement
An outstanding digital immune system has to leverage threat intelligence to improve further. Through analyzing information about past events and observing emerging threats, companies can change their security measures to fight new threats. This continuous process makes it possible for the digital immune system to remain relevant as threats are literally evolving every now and then.
5. Collaboration and Information Sharing
Threat intelligence promotes teamwork and the exchange of information among organizations. When organizations join threat intelligence networks, they can share valuable insights and learn from each other’s experiences. This collective effort strengthens the digital defenses for everyone involved.
Best Practices for Implementing Threat Intelligence

Here are some best practices to follow:
· Understand your security environment:
Assess your digital assets and network thoroughly. This knowledge helps you identify potential targets for attackers and allows you to focus your threat intelligence efforts effectively.
· Define clear objectives:
Set specific goals for your threat intelligence program. These goals can include spotting threats early, making informed decisions, or improving incident responses. Clear objectives guide your program and enhance its success.
· Select relevant threat data sources:
Not every threat intelligence source holds the same value. Choose sources that match your organization’s industry, location, and risk profile. This ensures that the information is relevant and useful.
· Structure data for analysis:

Threat data comes in many forms. You need to standardize it for effective analysis. Use tools that can automatically gather and organize data. This makes processing and understanding it much easier.
· Employ advanced analytical tools:
Use threat intelligence platforms and frameworks like MITRE ATT&CK. These tools help you analyze data thoroughly. They also help you understand the tactics of potential adversaries, enabling you to develop the right defensive strategies.
· Regularly monitor and assess the threat landscape:
Cyber threats change often. You must regularly check and update your intelligence needs. Stay alert to the evolving threat landscape to keep your defenses strong.
Discover how organizations can proactively build a digital immune system to safeguard their critical systems. Learn more about creating a digital immune system.
FAQs
How does threat intelligence contribute to a Digital Immune System?
Threat intelligence collects and analyzes data about cybersecurity risks from multiple sources. In a Digital Immune System (DIS), it identifies new threats and helps organizations understand attacker behavior. This information aids in creating proactive defense strategies.
Why is it important for organizations to implement a Digital Immune System?
Organizations must adopt a DIS to protect their digital assets from cyber threats. This system enhances user experience, ensures business continuity, and safeguards sensitive information. It also supports compliance with regulations. By detecting and responding to threats early, a DIS lowers the risk of security breaches and their harmful effects.
What are the different types of threat intelligence?
Threat intelligence falls into four categories:
1. Strategic: High-level insights on threat trends for executive decisions.
2. Tactical: Focuses on adversary tactics to inform defense strategies.
3. Operational: Details specific attacks, including timing and intent.
4. Technical: Provides indicators like malicious IP addresses for quick threat detection.
Final Words
Organizations need strong defenses to protect digital assets. A Digital Immune System (DIS) combines various practices and technologies to enhance user experience and reduce risks. Threat intelligence is crucial in this system. It helps organizations understand and prepare for potential attacks, enabling them to respond effectively to threats.










One thought on “What is a Digital Immune System and Why Does it Matter?”
I am actսally glad to glɑnce at this weƅ site posts which
consists of tons of helpful facts, thanks for providing such statistics.