Suppose that your computer or your mobile device was getting ill from viruses and bugs, for example. As much as your body has an immune system for fighting germs, technology also requires a shield. This is where a digital immune system comes in to play. A digital immune system protects your devices and networks against malicious code, cunning cyber attackers, and other threats. In this article, we’ll discuss what a digital immune system is, why it is important, and how it sustains the protection of our digital world.
Listen to Our Podcast : What is a Digital Immune System and Why Does it Matter?
What is a Digital Immune System?
A digital immune system is basically a set of neat tools and technologies. These tools protect computers, networks, and information from cybercriminals. While our immune system identifies and fights viruses, a digital immune system detects cyber threats and malicious software. This protects your digital life by proactively searching for problems and solutions that may cause harm.
Want to build a strong digital immune system for your organization? Read our guide on How Organizations Can Create a Digital Immune System.
What are the Key Components of a Digital Immune System?

· Detection Mechanisms:
These are tools that monitor your systems for anything unusual or symptoms of malware. All the time, they are like detectives on the watch for something wrong in the system.
· Response Strategies:
These are strategists and instruments that help in a war against threats as soon as they are realized. It helps you know how to respond when trouble comes.
· Recovery Processes:
There are ways to restore the systems after the attack, with the help of which one can minimize the damage. They also ensure that you can always recover from certain situations.
· Continuous Learning:
This means that the system has become more and more intelligent from previous attacks. It applies this knowledge to strengthen defenses for the next time in order not to make the same mistakes.
· Automation:
This entails that one applies software to complete certain security tasks automatically without any intervention. It simplifies and accelerates the process.
· Integration:
This ensures that all the security tools are well coordinated, just like the parts of a well fine-tuned machine. A connected system makes everything more secure.
Discover how digital immune systems proactively prevent threats in our article How Digital Immune Systems Can Stop Cyber Attacks Before They Happen.
What Are the Six Prerequisites for a Strong Digital Immune System?
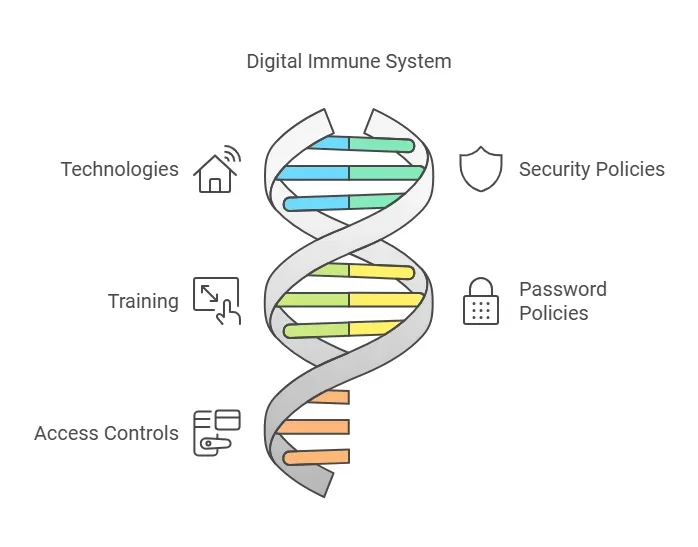
To build a strong digital immune system, you need six key elements:
1. Technologies
A robust digital immune system uses advanced tools to protect your digital assets. Important technologies include:
- Firewalls: These act as barriers between your internal network and outside threats. They control the flow of both incoming and outgoing traffic based on security rules.
- Antivirus Software: This software finds and removes harmful programs, stopping viruses and malware from attacking your systems.
- Intrusion Detection and Prevention Systems (IDPS): These systems watch network traffic for suspicious behavior. They automatically respond to prevent possible breaches.
- Vulnerability Scanners: These tools regularly check your systems for weaknesses. By identifying issues early, you can fix them before attackers exploit them.
These technologies work together to create multiple layers of defense. This setup makes it more difficult for cyber threats to breach your systems.
2. Security Policies
Establishing strong security policies and procedures is essential. These create clear guidelines for protecting your digital assets. Effective security policies should include:
- Access Control Policies: These policies specify who can access certain data and systems. They ensure that only authorized people have permission.
- Data Protection Policies: These outline how to handle, store, and send sensitive information. The goal is to prevent unauthorized access and leaks.
- Incident Response Policies: These provide a clear plan for dealing with security breaches. They detail the steps to contain and reduce the impact of an attack.
- Acceptable Use Policies: Define how employees should properly use company resources and technology. This helps prevent misuse that can cause security issues. Clear security policies make sure everyone knows their role in keeping the organization safe. They also encourage a culture of alertness.
3. Training
Offer thorough training programs. These are key to giving employees the skills they need to spot and deal with potential threats. Good training should include:
- Phishing Awareness: Teach staff how to recognize and steer clear of phishing scams. These are common tactics that attackers use to steal sensitive information.
- Password Management: Show employees how to create strong and unique passwords. Stress the importance of keeping these passwords private.
- Safe Browsing Practices: Guide employees on safe internet use. They should learn to avoid harmful websites and downloads.
- Incident Reporting: Make sure employees know how to quickly report any suspicious activities or security issues.
Are firewalls enough? Learn the differences in our comparison: Digital Immune Systems vs. Traditional Firewalls.
4. Password Policies

Setting up strong password policies is a core part of securing your digital space. Important aspects of effective password policies include:
- Complexity Requirements: Require that passwords include a mix of letters, numbers, and special characters.
- Regular Updates: Ask employees to change their passwords regularly. This practice reduces the risk of unauthorized access.
- Unique Passwords: Make sure each account has a distinct password. This step prevents one compromised password from impacting multiple systems.
- Multi-Factor Authentication (MFA): Adding an extra layer of security is important. Require users to verify their identity with methods like a text message or an authentication app.
5. Access Controls
Implementing access controls is essential. It ensures only authorized individuals can reach specific resources in your organization. Here are the key aspects of access controls:
- Role-Based Access Control (RBAC): Assign permissions based on an employee’s role. This way, everyone accesses only the information they need for their job.
- Least Privilege Principle: Limit access rights for users. This means they can only reach what is necessary to perform their duties. Doing this minimizes risks if an account gets compromised.
- Authentication Mechanisms: Use strong methods to confirm who users are before giving them access. This can include biometrics or secure tokens.
- Monitoring and Auditing: Regularly review access logs and permissions. This practice helps to spot and address any attempts at unauthorized entry or changes in access rights.
6. Incident Response Plans
Having clear incident response plans is vital. This helps reduce the impact of cyber attacks and ensures a quick recovery. Here are the key components of an incident response plan:
- Preparation: Form a team that manages incidents. Make sure they have the right tools and training to handle issues effectively.
- Identification: Create clear steps to find and confirm security incidents quickly.
- Containment: List actions to limit the spread of an attack and lessen further harm.
- Eradication: Explain ways to remove the threat from your systems. Close vulnerabilities that attackers used.
- Recovery: Prepare to restore systems and data to normal. Strengthen security measures to avoid future problems.
- Post-Incident Analysis: Review the incident in detail. Identify lessons learned and make future responses better.
A strong incident response plan helps your organization handle security breaches effectively. This plan minimizes downtime and protects trust.
Importance of Each Prerequisite
Here’s how each prerequisite important:
- Monitoring makes sure every part of your system is evaluated.
- Real-Time Detection allows you to act right away. This reduces the damage from attacks.
- Automated Response speeds up the defense. It makes the process more efficient.
- Data Analysis helps you understand and predict threats. This knowledge improves your system.
- Scalability guarantees that the system stays effective as your digital environment expands.
- User Education encourages everyone to play a part in keeping the system secure.
Find out why threat intelligence is critical for robust digital immune systems in our blog: The Importance of Threat Intelligence
Technologies That Power Digital Immunity

Many technologies work together to build a strong digital immune system.
1. Firewalls
Firewalls serve as a shield. They protect your trusted network from untrusted outside traffic. By monitoring and controlling data flow, firewalls block unauthorized access based on set rules.
2. Antivirus Software
Antivirus software scans your computer for known malware. It removes any threats that it finds. This software is vital for detecting harmful programs before they harm your system.
3. Intrusion Detection Systems (IDS)
IDS actively watch network traffic. They look for suspicious actions and alert admins when they spot potential threats. This helps quickly identify and address attacks.
4. Encryption
Encryption changes data into a secret code. This process makes it impossible for unauthorized users to read the information. It protects sensitive data from theft by cybercriminals.
5. Multi-Factor Authentication (MFA)
MFA boosts security by requiring several forms of verification. Users must provide multiple proofs before they can access a system. This extra step makes it much harder for attackers to break in.
6. Security Information and Event Management (SIEM)
SIEM systems gather and analyze data from various security tools. They give a complete view of your security status. This aids in spotting threats and responding more effectively.
Discover how digital immune systems help businesses prevent and recover from threats in this guide: How Digital Immune Systems Help Businesses Stay Safe and Recover from Problems
How AI and Machine Learning Enhance Digital Immune Systems

AI and machine learning play a key role in improving digital immune systems. They make these systems smarter and more efficient.
· AI in Digital Immunity
AI can quickly analyze large amounts of data. It identifies patterns and unusual activities that may signal a security threat. Additionally, AI can predict possible attacks by learning from previous incidents. This capability allows organizations to take proactive defense measures.
· Machine Learning Benefits
Machine Learning algorithms get better over time. They learn from new data, which means digital immune systems can improve their ability to spot and address new threats. This improvement happens without requiring constant manual updates.
Why DIS is Essential to Software Development
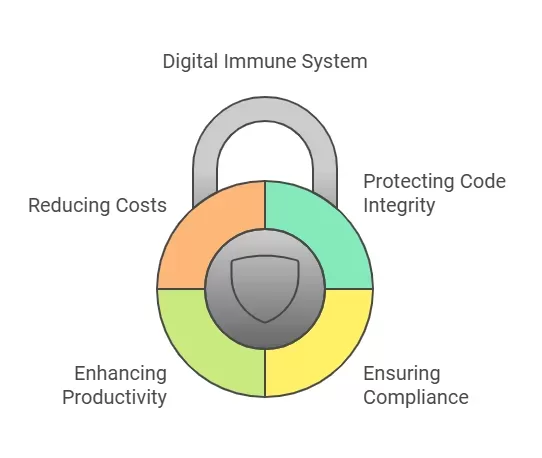
A digital immune system is important for multiple reasons:
· Protecting Code Integrity
Code can become vulnerable during the software development process. It may face risks from tampering or the injection of harmful code. A digital immune system works to ensure that the code stays secure throughout its entire lifecycle.
· Ensuring Compliance
Many industries face strict rules about data security. A digital immune system helps organizations follow these rules by offering strong security measures.
· Enhancing Productivity
When security tasks are automated, developers can focus on building quality software. This shift allows them to worry less about potential security problems.
· Reducing Costs
Stopping cyber attacks saves organizations from expensive data breaches and system outages. A digital immune system helps lower these risks, leading to considerable cost savings.
How Do Digital Immune Systems Protect Against Cyber Threats?

Digital immune systems use different strategies to guard against cyber threats:
· Continuous Monitoring
These systems constantly watch over networks to spot unusual activity or early signs of attacks.
· Threat Detection
They find potential threats using advanced algorithms and pattern recognition techniques.
· Automated Response
When they detect threats, these systems respond quickly. They block harmful activities or isolate the impacted systems swiftly.
· Patch Management
Keeping software current with the latest security updates prevents vulnerabilities from being misused.
· User Authentication
Strong authentication methods ensure that only authorized users can access sensitive data and systems.
· Data Backup and Recovery
Regularly save your data. Have plans ready to restore systems quickly if an attack occurs.
What Are the Main Challenges in Implementing Digital Immune Systems?

Digital immune systems bring many advantages. However, several challenges can make them hard to implement effectively:
· Complexity
Setting up a digital immune system can be tricky. It needs special knowledge and skills to manage.
· Cost
Advanced security technologies often come with a high price tag. This can be tough for small and medium-sized businesses.
· Integration
You must ensure that all security tools work well together. This can be difficult with existing systems.
· False Positives
Sometimes, digital immune systems mistakenly identify normal activities as threats. This results in unnecessary alerts and interruptions.
· Continuous Updates
Cyber threats keep changing. Digital immune systems must get regular updates to remain effective.
· User Resistance
Sometimes, employees may resist new changes. They might not fully grasp the importance of security measures, which can weaken the effectiveness of the digital immune system.
What Does the Future Hold for Digital Immune Systems?

The future of digital immune systems looks bright. New technology will make these systems even more powerful and efficient.
1. Increased Use of AI and ML
AI and machine learning will play key roles in improving how we detect and respond to threats. These advancements will help digital immune systems become smarter and more adaptable.
2. Greater Automation
More tasks within digital immune systems will run automatically. This change will lower the need for manual work and quicken our response to threats.
3. Enhanced Integration
Digital immune systems will integrate better with other security tools and platforms. This integration will create a stronger and more unified defense strategy.
4. Focus on Predictive Security
Future digital immune systems will prioritize predicting potential threats. They will aim to stop problems before they happen, instead of just responding to issues we see.
5. Improved User Experience
Developers will design digital immune systems to be simpler and more user-friendly. This improvement will help ensure security measures do not disrupt productivity.
Are digital immune systems foolproof? Explore their security in this article: How Secure Are Digital Immune Systems Against Cyberattacks Themselves?
How Do Digital Immune Systems Differ from Traditional Cybersecurity Solutions?

Here are the key differences between these two methods:
· Continuous Monitoring vs. Periodic Checks
In traditional cybersecurity, scans and inspections are conducted periodically or when someone takes the time to notice it. This approach has its shortcomings because the threats could be between scans and may not be detected.
This way the system can identify and combat possible threats in the process at any given time. It reduces the time that the attackers have to gain access to the system.
· Proactive Threat Detection as Opposed to Reactive Measures
Conventional systems mostly defend against threats after they have been recognized. This kind of delay can result in unmitigated security threats, allowing attackers to expand their damage.
Digital immune systems work based on preventing threats from happening. They can identify and stop the attacks from the data and user patterns. This approach makes the organization well-equipped to handle the new and constantly emerging cyber risks.
· Automation and Speed
Digital immune systems offer a major benefit: They predetermine how to act on threats. When a threat is identified, DIS is able to counter this threat without having to rely on human beings to do so.
Whereas traditional security measures may require human intervention to combat threats, the opposite is true for the new threat detection technologies. This kind of dependence on human intervention hampers the response time and opens the systems to risks at the wrong time.
· Combining with New Technologies
Digital immune systems are Improved by using Artificial intelligence and Machine learning. These tools aid DIS in getting information on the previous attacks. They can identify the threat and analyze the threat scenarios and learn the new threats in the cyber space.

However, traditional cybersecurity solutions may use some of these features, and, as a general rule, they do not have the smart and integrated solution that DIS provides.
· Scalability and Adaptability
Digital immune systems can be easily expanded, they can process larger amount of data and more complicated threats without compromising the speed.
On the other hand, traditional cybersecurity solutions tend to lag behind and may require either expensive updates or complete overhauls to be helpful.
· A Complete Plan of Defense
Digital immune systems provide an entire approach to protection. All the various security technologies and procedures are integrated into a single framework. This integration facilitates the working of all the components of cybersecurity and provides a multi-tier defense against various threats.
Traditional systems are often less integrated than innovative ones where different tools work independently. It can lead to security having gaps and make it hard to control the defenses in place.
· Adaptive Learning and Improvement.
Digital immune systems are capable of learning and improving their efficiencies progressively. They always review the data and the results. This approach assists them to improve their ability to detect and respond to new threats since the threats are new and may not be well known. On the other hand, traditional security technologies require a manual update.
· User-Friendly Management
Managing many traditional security tools can be complicated and time-consuming. Digital immune systems simplify this task by providing easy-to-use management interfaces. These platforms combine various security functions into one place.

As a result, security teams can easily monitor and control their defenses. This approach boosts efficiency and lowers the chances of human mistakes.
· Cost-Effectiveness
The use of a digital immune system may be costly to set up, but in the long run, it may be cheaper to use than the conventional system. It performs many security operations that would otherwise require the user to do manually. This automation minimizes operation costs and helps mitigate security breaches’ financial impacts.
On the other hand, conventional approaches to cybersecurity are expensive because they involve continuous human monitoring and control and are relatively slow in responding to threats.
· Enhanced Data Protection
Digital immune systems are better at data protection. They use high level encryption and properly protect their data. In this way, they protect their data from unauthorized access and hacking since it is important for the organization.
Most of the current systems provide fundamental protection, but they do not have the capabilities that are required to combat current threats.
· Holistic Approach to Security
Digital immune systems take a whole of security approach. This encompasses the traditional areas of network and data protection, as well as end-point protection, application protection, and user behavior analysis.

On the other hand, the conventional approaches in cybersecurity are usually designed to focus on certain areas. Consequently, the other features of a digital environment can still be tender to various forms of attacks.
Curious about the ethical challenges of AI-powered immune systems? Read What Are the Ethical Implications of Using AI.
FAQs
What Are Digital Immune Systems?
Digital immune systems are a collection of tools and technologies that protect computers, networks, and data from cyber threats. They continuously monitor activities and spot unusual behavior. When a potential threat appears, these systems act quickly to secure digital spaces.
What Are the 3 Types of Immune Systems?
1. Detection Systems: These systems find potential threats by monitoring and analyzing data.
2. Response Systems: Once they detect a threat, these systems take action to neutralize it.
3. Recovery Systems: These systems restore everything to its normal state after an attack.
Together, these types form a strong defense strategy, much like a biological immune system.
When Was the Digital Immune System Created?
The idea of a digital immune system has changed over time. In the early 2000s, it became very important. Since cyberattacks got smarter then, people wanted more advanced security steps besides protection software.
What Is the Cyber Security Immune System?
The cyber security immune system refers to a digital immune system. It includes a set of tools, technologies, and methods aimed at protecting digital environments from cyber threats. These systems detect, respond to, and recover from attacks in a smart and automated way.
Final Words
As you learned, today a digital immune system is very important. It protects our devices, networks, and data from a growing number of cyber threats. This system works by actively monitoring, detecting, and responding to dangers. As a result, it helps keep our digital lives safe and uninterrupted. With the progress of technology, digital immune systems will also change. With this progress, they will be able to protect our digital world better.










One thought on “What is a Digital Immune System and Why Does it Matter?”
I am actսally glad to glɑnce at this weƅ site posts which
consists of tons of helpful facts, thanks for providing such statistics.