This pillar page will give you a full view of the topic social engineering. Here we discuss, what it is, the types of attacks, and how to stay safe from them. So, this guide will help you understand what social engineering is, how it works, and (if you already know what it is) how to defend yourself against being the victim of it, whether you’re just learning or you’re an old hand. The sections are for clear info and useful tips!
Social engineering is a way by which the wrongdoers manipulate people into surrendering their data. Unlike in the movies where they use technical prowess to penetrate into systems, they exploit human personalities. This means man uses feelings, trust and fear for the purpose of achieving goals.
It is about winning the trust. One common tactic that is frequently used is when the attacker feigns to be the target, or an organization the target deals with. In this way, the attackers weaken the target’s defenses and get an opportunity to obtain passwords, personal data, etc.
Want to safeguard against cyber threats? Discover essential best practices for online security to keep your information safe. Read our guide what is social engineering in cybersecurity?
How Does Social Engineering Work?

Social engineering is a technique employed by attackers in a process of convincing victims to disclose information or do something that is otherwise undesirable. Social engineering is different from technical hacking where one depends on skill in systems’ loopholes as a way of hacking into a system. Here’s a breakdown of how social engineering works:
1. Information Gathering
The initial phase of a social engineering attack involves collecting information. Their targets involve obtaining information from social media platforms, official organization’s website, and new articles. It also helps the target build a general picture of the target environment in terms of key people, organizational chart, etc.
Techniques:
- LinkedIn or Facebook for instance can be used to search for more information about the targets of an attack.
- It can be used as a tool to obtain information on employees, departments and working processes.
2. Establishing Trust
The next stage that attackers adopt after they have gathered enough information is to build trust. This includes initiating communication with the target and introducing oneself as someone reliable, e.g. a co-worker, IT administrator, or a member of a credible organization.
Approaches:
- It will also be a tactic to make some pretensions of being friendly in order to make the targets comfortable talking and lowering their security.
- From the information obtained earlier, they designed it in a way that makes it more convincing. They have one for each of the earlier categories.
3. Exploitation
It is expected that once the attacker has gained the victims’ confidence, the latter will compel them to act unsafely. This could involve clicking on malicious links, providing sensitive information, or performing tasks that compromise security.
Common Tactics:
- Creating a sense of urgency can prompt quick decisions without careful consideration.
- Attackers may invoke fear or excitement to push victims into acting quickly.
Techniques Used in Social Engineering

Attackers employ various techniques to achieve their goals:
Phishing: Falsely sending emails, which seem real enough to catch victims to give out sensitive information.
Vishing (Voice Phishing): It uses phone calls to impersonate trusted figures in order to get information.
Smishing (SMS Phishing): Calling or text messaging people with links or requests for personal data.
Pretexting: Finding ways to create believable scenarios to get victims to share their sensitive information.
Baiting: Something enticing (like free software) to lure people into giving up personal details.
Wondering how phishing compares to social engineering? Discover the differences in our detailed article on Social Engineering vs Phishing.
Want to learn how people are getting tricked by attackers? The next section discusses each of these techniques used in social engineering in more details. You’ll learn about phishing, vishing, smishing, pretexting, and baiting: how it happens and how to recognize it. So, keep reading!
What are Common Types of Social Engineering Attacks?

Social engineering attacks utilize psychological manipulation to deceive people into disclosing confidential information or taking actions that undermine security. Below are some of the most prevalent forms of social engineering attacks:
1. Phishing
Phishing is the most widespread type of social engineering attack. Attackers send fraudulent emails that appear to come from legitimate sources, such as banks or well-known companies. These emails often contain links to fake websites designed to steal personal information, like usernames, passwords, or credit card numbers.
Characteristics:
- Looks like a legitimate email.
- Often includes urgent requests for action.
- May ask for sensitive information directly.
2. Spear Phishing
Spear phishing is a more focused form of phishing. Instead of sending mass emails, attackers research specific individuals or organizations and write personalized messages. This makes the attack more convincing and increases the chances of success.
Characteristics:
- Tailored to specific individuals.
- Uses personal information to build trust.
- Often targets high-profile individuals (executives).
3. Baiting
Baiting involves offering something enticing to lure victims into providing information or access. This could be a free download, a prize, or any other attractive offer that prompts the victim to act without thinking.
Characteristics:
- It can occur online or in physical spaces.
- Often promises rewards in exchange for sensitive data.
- Exploits curiosity or greed.
4. Pretexting
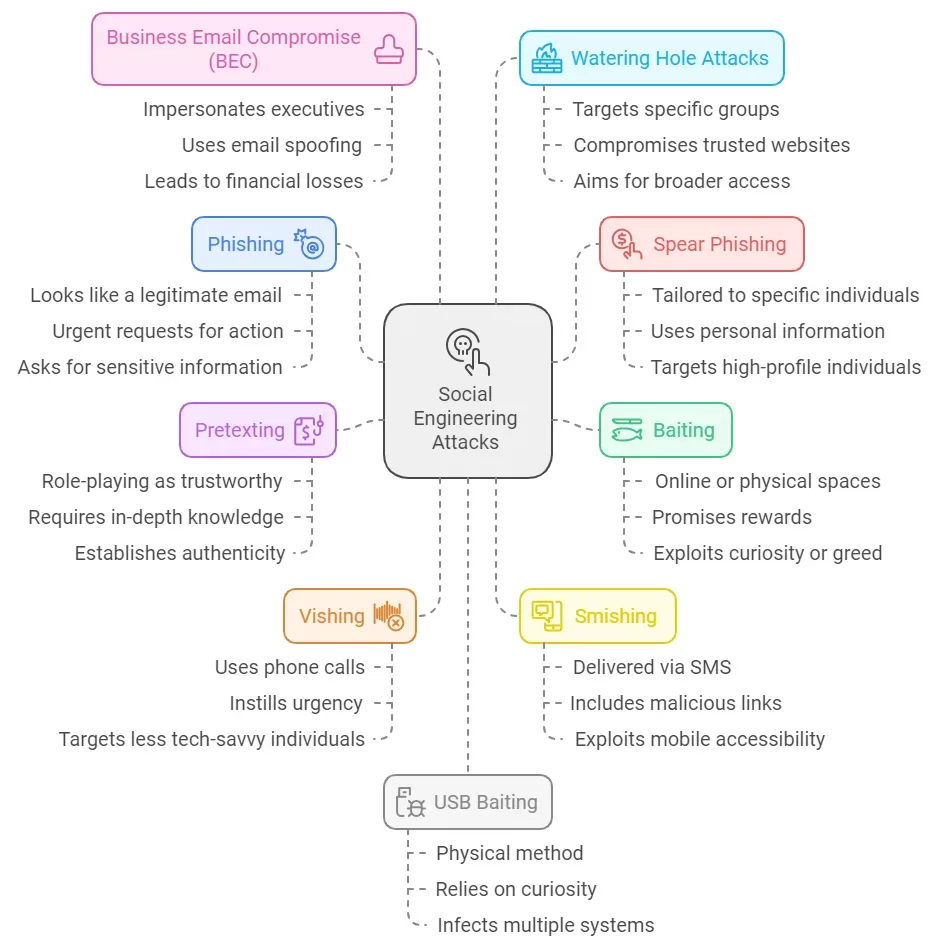
Types of social engineering: a detailed overview
In pretexting, the attacker creates a fabricated scenario (or pretext) to obtain information from the victim. This could involve impersonating a trusted authority figure, such as a bank employee or IT technician, to gain access to sensitive data.
Characteristics:
- Involves role-playing as someone trustworthy.
- Often requires in-depth knowledge about the target.
- Seeks to establish a sense of authenticity.
5. Vishing (Voice Phishing)
Vishing is a type of social engineering that occurs over the phone. Attackers call victims and pose as legitimate organizations, such as banks or government agencies, urging them to provide personal information.
Characteristics:
- Uses phone calls instead of emails.
- Frequently instills a feeling of urgency or concern.
- Targets individuals who may be less tech-savvy.
6. Smishing (SMS Phishing)
Similar to vishing, smishing uses text messages to deceive victims into revealing personal information. Attackers may send messages claiming there’s an issue with an account or offering rewards for clicking on a link.
Characteristics:
- Delivered via SMS messages.
- Often includes links to malicious websites.
- Exploits immediate accessibility of mobile devices.
7. Business Email Compromise (BEC)
BEC attacks involve impersonating a high-level executive within an organization to trick employees into transferring money or sharing sensitive data. Attackers often use email spoofing techniques to make their requests appear legitimate.
Characteristics:
- Targets businesses and organizations.
- Often involves impersonating executives or suppliers.
- This can lead to significant financial losses.
8. Watering Hole Attacks
In watering hole attacks, attackers compromise websites that are frequently visited by specific groups (like employees of a particular company). When members of that group visit the infected site, they may unknowingly download malware onto their devices.
Characteristics:
- Targets specific groups based on their online behavior.
- Involves compromising trusted websites.
- Aims for broader access once one device is compromised.
9. USB Baiting
This method involves leaving infected USB drives in public places, hoping someone will pick them up and plug them into their computers. Once connected, the malware can spread through the organization’s network.
Characteristics:
- Physical method of attack.
- Relies on curiosity about found items.
- Can infect multiple systems quickly.
Understanding these common types of social engineering attacks is crucial for both individuals and organizations to recognize potential threats and take appropriate precautions.
Protect yourself from cyber threats. Read our guide on What Is Phishing and How to Prevent It.
Why is Social Engineering So Dangerous?

Social engineering poses a significant threat because it exploits human psychology rather than relying solely on technical vulnerabilities. Here are some key reasons why social engineering is particularly dangerous:
1. Bypassing Security Measures
Attackers can easily bypass traditional cybersecurity defenses by tricking individuals into revealing sensitive information. Unlike malware or hacking attempts that require technical skills, social engineering relies on deception and manipulation. This means that even the most secure systems can be compromised if an attacker successfully deceives a user into providing access or data.
2. Exploitation of Trust
Social engineers exploit the natural tendency of people to trust others. They often impersonate trusted figures, such as colleagues, IT support, or representatives from legitimate organizations. This creates a false sense of security. Moreover, this makes it easier for them to extract sensitive information or persuade victims to take harmful actions.
3. High Success Rate
Statistics show that a staggering 98% of cyberattacks involve some form of social engineering. This high success rate is due to the psychological tactics used by attackers, which can manipulate even the most cautious individuals into making mistakes.
4. Wide Range of Techniques
Social engineering attacks come in many forms, such as phishing emails, vishing (voice phishing), smishing (SMS phishing), baiting, and pretexting. Each of these techniques targets different vulnerabilities and can be tailored to specific individuals or organizations, making them highly effective.
Learn how email security can combat social engineering. Read about the Importance of Social Engineering in Email Security.
5. Severe Consequences
The consequences of a successful social engineering attack can be catastrophic. Attackers may gain access to sensitive data, financial information, or even entire systems. This can lead to identity theft, financial loss, reputational damage, and unauthorized access to confidential information. The consequences can extend beyond the immediate victim to affect entire organizations and their customers.
6. Difficult to Detect
Many social engineering attacks are subtle and can go unnoticed until significant damage has occurred. Victims may not realize they have been manipulated until it’s too late, making detection and prevention challenging
How to Prevent Social Engineering

Combating social engineering involves raising awareness, providing training, and taking proactive steps to protect against potential threats. Here are some effective strategies:
Awareness Training
· Educate Employees:
Organizations should conduct regular training sessions to help employees recognize social engineering tactics. Being informed serves as the most crucial defense mechanism.
· Simulated Attacks:
Conducting mock phishing campaigns can help employees practice identifying suspicious emails or messages without real-world consequences.
Strong Security Practices
· Verify Requests:
Encourage individuals to verify any requests for sensitive information through a separate channel. For example, if they receive a suspicious email, they should call the organization directly using a known number.
· Use Multi-Factor Authentication (MFA):
Multi-factor authentication (MFA) enhances security by introducing extra verification steps in addition to a password.
Secure Personal Information
· Limit Sharing on Social Media:
Encourage individuals to be cautious about sharing personal information online that could be used against them in a social engineering attack.
· Regularly Update Passwords:
Using strong, unique passwords for different accounts can help reduce the risk if one account is compromised.
Incident Response Plan
· Have a Response Plan:
Organizations should have a clear plan in place for responding to suspected social engineering attempts. This includes reporting procedures and steps for mitigating damage.
By applying these protective steps, individuals and organizations can significantly reduce their vulnerability to social engineering attacks.
Social media is a common target for hackers. Discover more in our post on How Hackers Use Social Media for Social Engineering Attacks.
Notable Social Engineering Incidents

Learning from past incidents can provide valuable insights into how social engineering attacks operate and their potential impact. Here are a few notable cases:
1. Equifax Breach Help Websites
In 2017, Equifax, one of the largest credit reporting agencies in the U.S., suffered a massive data breach that exposed sensitive personal information of approximately 147 million people. This incident is a prime example of how social engineering can lead to significant security failures.
What Happened?
Data Compromise: Hackers exploited a vulnerability in Equifax’s web application framework. They accessed names, Social Security numbers, birth dates, addresses, and even some driver’s license numbers.
· Response:
In the aftermath, Equifax set up help websites to assist affected individuals. However, these sites faced criticism for being poorly designed and difficult to navigate. Many users reported issues when trying to freeze their credit or access their accounts.
· Impact:
The breach led to widespread identity theft concerns and prompted legal actions against Equifax. The company eventually agreed to pay up to $700 million in fines and compensation.
Lessons Learned:
- Organizations must prioritize regular security updates and vulnerability assessments.
- Providing clear, accessible support during crises is essential for maintaining trust.
2. 2016 United States Elections Leaks
The 2016 U.S. elections were marred by significant leaks of sensitive information through social engineering tactics. Hackers affiliated with Russian military intelligence infiltrated various political organizations, leading to widespread chaos during the election season.
Key Events:
· Hacking of DNC:
Hackers accessed the Democratic National Committee’s (DNC) systems and stole over 20,000 emails. These emails were later published by WikiLeaks just before the Democratic National Convention, causing turmoil within the party.
· Use of Guccifer 2.0:
The hackers created a persona named Guccifer 2.0 to release stolen documents and distract attention from their activities. This tactic played on public curiosity and media coverage.
Impact on Campaigns:
The leaks created negative media cycles for Hillary Clinton’s campaign and shifted focus away from key issues. The controversy surrounding the leaks contributed to significant political division and distrust among voters.
Lessons Learned:
Political organizations must train staff to recognize phishing attempts and other social engineering tactics.
Having a plan in place for handling leaks can help mitigate damage and maintain public trust.
Explore the role of social engineering in social work. Learn more in our blog on What Is Social Engineering in Social Work.
3. The Target Data Breach (2013)
In one of the largest retail data breaches, attackers used social engineering to gain access to Target’s network. They sent a phishing email to a third-party vendor, tricking an employee into revealing their login credentials. This breach led to the theft of credit card information from over 40 million customers.
4. The RSA Security Breach (2011)
RSA, a well-known security company, fell victim to a social engineering attack when employees received phishing emails disguised as legitimate messages. One employee opened an infected Excel file, allowing attackers to steal sensitive data related to RSA’s SecurID two-factor authentication products. This breach compromised numerous organizations that relied on RSA’s security systems.
5. The Twitter Bitcoin Scam (2020)
In July 2020, several high-profile Twitter accounts were hacked in a coordinated social engineering attack. Attackers used social engineering techniques to manipulate Twitter employees into granting access to internal tools. They then posted fraudulent messages promoting a Bitcoin scam, resulting in significant financial losses for victims.
These incidents highlight the effectiveness of social engineering tactics and the potential consequences for individuals and organizations alike.
How Does Social Engineering Compare to Traditional Malware?

Understanding the differences between social engineering and traditional malware is crucial for developing effective security strategies. Here’s a comparison:
| Feature | Social Engineering | Traditional Malware |
| Method of attack | Manipulates human behavior | Uses software vulnerabilities |
| Target | Individuals or employees | Systems and networks |
| Skill requirement | Psychological manipulation | Technical knowledge |
| Detection | Often goes unnoticed until damage occurs | Can be detected by antivirus software |
| Impact | Loss of sensitive information | System damage or data corruption |
So, both methods aim to compromise security. However, they use different approaches. Social engineering relies on exploiting human trust, while traditional malware focuses on exploiting technical weaknesses.
Examples of Social Engineering Attacks

To better understand social engineering, it’s important to look at specific examples.
Example 1: Phishing Email
A common phishing attack involves an email that appears to be from a trusted source, like a bank. The email may state that there is an issue with the recipient’s account and urges them to click on a link to resolve it. Once clicked, the link leads to a fake website that looks like the bank’s official site. The victim is prompted to enter sensitive information, such as their username and password.
Key Points:
- Looks legitimate
- Urges immediate action
- Collects sensitive data through fake websites
Example 2: Pretexting Phone Call
In a pretexting attack, an attacker might call an employee at a company and pretend to be from the IT department. They might say there’s an urgent need to verify the employee’s login credentials due to a supposed system upgrade. The employee, trusting the caller, provides their username and password, giving the attacker access to sensitive company information.
Key Points:
- Involves direct communication
- Creates a false scenario for urgency
- Exploits trust in authority figures
Example 3: Baiting with USB Drives
Baiting involves leaving infected USB drives in public places, such as parking lots or coffee shops. Individuals may pick up these drives and plug them into their computers, thinking they’ve found something valuable. However, these drives contain malware that can compromise their systems and steal data.
Key Points:
- Physical method of attack
- Relies on curiosity
- Can infect multiple systems quickly
These examples illustrate how social engineering can take many forms and highlight the importance of vigilance in recognizing potential threats.
Social engineering plays a crucial role in societal development. Find out more in How Does Social Engineering Work in the Development of Society.
How to Detect Social Engineering Attacks

Detecting social engineering attacks can be challenging since they often mimic legitimate communications. However, there are several warning signs to look out for:
Suspicious Communication
· Unusual Requests:
Be wary of unexpected requests for sensitive information, especially if they come from unfamiliar sources or seem out of character for the sender.
· Poor Grammar or Spelling:
Phishing emails often include grammar mistakes or unusual wording. Legitimate organizations typically proofread their communications.
Urgency and Pressure Tactics
· Too Good to Be True Offers:
It probably is if something seems too good to be true (like winning a prize). Attackers often use enticing offers to lure victims.
· Immediate Action Required:
Be wary of any messages that urge you to take immediate action. Legitimate organizations usually allow time for verification.
Verify Before Acting
· Check Email Addresses:
Look closely at email addresses for slight misspellings or unusual domains that may indicate a scam.
· Call Directly:
If you receive a suspicious request via email or phone, contact the organization directly using known contact information rather than responding directly.
Businesses should be aware of these signs and take proactive steps to verify requests. So, they can better protect themselves against social engineering attacks.
FAQs About Social Engineering
What Is Social Engineering in Simple Words?
Social engineering is when someone tricks you into giving up personal information or access to your accounts. Instead of using technology to hack into systems, they use manipulation and deceit to get what they want.
Is Social Engineering Illegal?
Yes, social engineering is illegal. It involves deceitful practices to gain unauthorized access to sensitive information or systems. Many countries have laws against fraud and identity theft that cover social engineering tactics.
What Percentage of Hackers Use Social Engineering?
Studies show that a significant percentage of cyber-attacks involve social engineering. Estimates suggest that around 90% of successful data breaches involve some form of social engineering, highlighting its effectiveness.
What Is the Most Widespread Type of Social Engineering?
Phishing represents the most widespread type of social engineering. It involves sending fraudulent emails that appear legitimate to trick individuals into revealing sensitive information. Phishing attacks can target anyone and make them widespread and dangerous.
How Much Does a Social Engineering Attack Cost?
The cost of a social engineering attack can vary widely based on the scale and impact. On average, organizations may face losses ranging from thousands to millions of dollars due to data breaches, legal fees, and loss of customer trust. According to some studies, the average cost per stolen record can exceed $150. This leads to substantial financial implications for businesses.
Final Words
Social engineering is a serious threat that exploits human behavior rather than technical vulnerabilities. By understanding how these attacks work and implementing preventive measures, individuals and organizations can better protect themselves against manipulation and deceit.
Awareness, education, and vigilance are key in combating social engineering. If something seems suspicious or too good to be true, it’s always best to verify before taking action.