Hackers use social media to gather details about their targets. Information relating to people, especially their identity is often passed through these platforms. They do this very often without fully appreciating the dangers it comes with. This information is very useful to hackers because it helps them design their social engineering attacks. Here are some common ways they trick people:
Listen to Our Podcast: Hackers & Social Engineering on Social Media
1. Collecting People’s Data
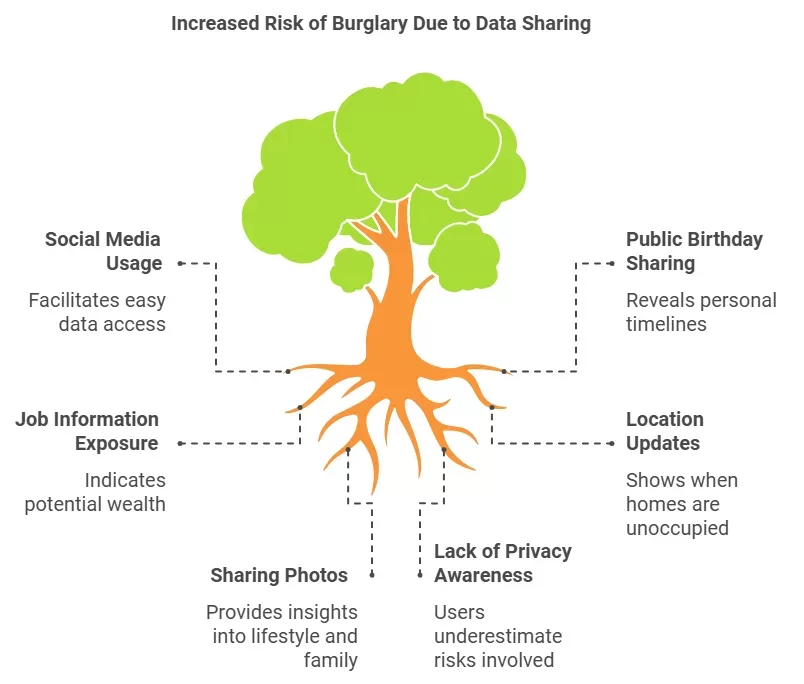
Burglars gather information about a person before they commence an attack. Social media makes this easy. People often share personal details like:
- Birthday: A large number of people use profiles and many of them indicate their birthday in the profile.
- Job Information: LinkedIn for example provides profiles that have a job description, company name, and experience.
- Location: People use status updates to share location updates, places they currently are, and places they go.
- Photos and Family Details: A picture can tell you about family members, pets, or hobbies.
For example, a hacker notices an individual wearing a company ID while she posts a picture on her social media account. This detail can substantiate their workplace. Hackers can then immediately log in as a co-worker.
In our guide ”Importance of Social Engineering in Email Security” you can learn why social engineering is a growing threat to email security and how you can safeguard your inbox from these attacks!
2. Creating Fake Profiles
Hackers use fake profiles for social engineering in many ways:
- Impersonating a Friend or Family Member: This may make them believe they are persons familiar with the target. This could be a relative or a friend. This disguise makes the victim be cheated by them.
- Fake Company Profiles: They come up with fake accounts mimicking actual companies. Perhaps some might use it to lure people through fake employment offers or fake discounts.
For instance, a hacker could mint an account of himself pretending to be a company’s recruiter. They would contact a job seeker, request to provide personal details or send a link to a virus/SPAM. This happens under the disguise of a “job application process.”
3. Phishing Scams Through Direct Messages

Phishing on social media often works like this:
- Fake Links: Phishers then provide links that seem to direct to an actual website. However, when someone clicks the link, it directs them to a fake site that steals their information.
- Urgent Messages: Messages often create a sense of urgency. They might say, “Your account is at risk! Click here to secure it.” People feel anxious about their security and are likely to click such messages.
Example: A hacker may pretend to be from Instagram. They could say, “Your account will be suspended soon unless you confirm your password.”
Want to protect yourself from phishing scams? Read our guide on recognizing and stopping phishing attacks before they reach you!
4. Like and Share Baiting
Hackers use social media posts to encourage people to “like” or “share” a post to win a prize or get something for free. These posts may appear harmless, but they can pose hidden risks.
Hackers gather a list of users who interact with the post. They use this information to plan future attacks. Additionally, some links in posts lead to malicious websites that install harmful software on users’ devices.
Example: A common trick is a post claiming, “Share this post and win a new smartphone!”
5. Exploiting Privacy Settings

Hackers often exploit privacy settings in various ways:
1. Viewing Public Profiles: They can see personal details, photos, and posts on public profiles without needing a friend request.
2. Using Shared Connections: If a hacker and a target have mutual friends, the hacker can send a friend request without raising suspicion. Once connected, they gain access to more information.
3. Tracking Posts and Locations: Hackers monitor posts to learn about a target’s routines, favorite spots, and upcoming events.
Example: If a user’s posts are public, a hacker may see a post that says, “Going on vacation tomorrow!”
Confused about social engineering and phishing? Explore our guide ”Social Engineering vs Phishing” to understand the difference and stay protected
Using Social Media Challenges and Games
Hackers use social media challenges for their attacks in several ways:
1. Getting Password Hints: People often use details like pet names or birthdays for passwords. Hackers can gather this information from challenge responses.
2. Building Trust: Some challenges come from fake accounts pretending to be friends. Once a hacker engages a target, they may ask for more personal information.
Example: A popular post might ask, “Your spy name is your first pet’s name + your mom’s maiden name!”
Tracking Activity Through Likes and Comments

Hackers track users’ activity in several ways:
1. Learning Relationships: They monitor who interacts frequently with the target. This helps identify close friends and family.
2. Observing Daily Habits: By noticing when a person is active on social media, hackers can understand their routine. This makes it easier to anticipate when they might respond to messages.
3. Discovering Interests: Hackers analyze likes and comments to learn about a person’s interests. They can then tailor phishing messages to seem more convincing.
Example: If a hacker sees someone liking many travel-related posts, they might send a fake “free travel offer” message to trick them into clicking a harmful link.
Read our blog ”What is Social Engineering in Cybersecurity?” to learn how social engineering tricks can compromise your security and how to defend against cyber threats!
FAQs
Why is social networking a social engineering threat?
Social networking allows hackers to gather personal information. This makes it easier for them to trick people into sharing private details.
What do hackers do with your social media?
Hackers use social media accounts to steal data. They may impersonate you or trick your contacts into sharing information or money.
How can hackers use your photos on social media?
Hackers can use your photos to create fake profiles. They may also gain information about your location, friends, and lifestyle.
What should you avoid sharing on social media to stay safe?
Avoid sharing sensitive details like your home address, travel plans, financial information, or answers to common security questions (like pet names or birthdays).
Curious about how social engineering manipulates victims? Read our detailed blog ”What is Social Engineering and How Does It Work?” to learn how it works and ways to stay safe!
Final Words
Social media can connect us, but it also carries risks. Hackers use these platforms to gather personal information and trick people. By understanding their tactics, like fake profiles and phishing messages, we can protect ourselves. Staying alert, using privacy settings, and avoiding oversharing are simple steps to enhance your safety.