Thousands of messages are sent every day. These include messages containing personal information, personal messages, as well as the fiscal data. Since emails have found their way into everyday use, they have also become potential victims of cybercriminals. Another technique through which hackers gain access to some organizational data is social engineering. It makes people disclose information or do something that is not safe without their willing. Here, we’ll discuss the relationship between social engineering and email security, the strategies employed in email attacks and the possible measures that people as well as firms can take to avoid falling prey to such attacks.
Listen to Our Podcast: Social Engineering and Email Security Threats
What is Social Engineering in Email Security?
Social engineering in email security is based on the concept that the goal is to deceive people. Unlike other risky attacks such as the weak spot that is searched in systems or networks, social engineering takes advantage of the mind. Social engineering emails look artificial and are usually created to mimic like real messages. They may appear as coming from familiar people or require some action immediately. This make it difficult for people to realize that it is a trick being pulled on them.
Common Types of Social Engineering Attacks in Email Security
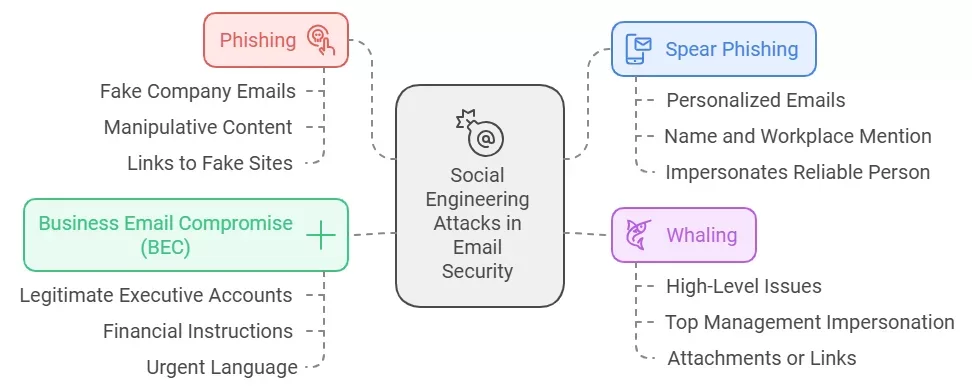
There are various kinds of social engineering that are aimed directly at people who use email. Each method takes advantage of different tendency or emotion of people. Let’s examine the most common types:
1. Phishing
Characteristics of Phishing Emails:
– They seem to be real e-mails from such recognized companies.
– They still can be quite manipulative, like when they inform on the possibility of your account being suspended.
– Some are links that lead to sites fakes whose aim is to steal your information.
Want to protect yourself from phishing attacks? Read our blog to learn what phishing is and how you can prevent it today!
2. Spear Phishing
Characteristics of Spear Phishing Emails:
- They are individual and particular.
- They usually greet the victim by his or her name and may mention the victim’s workplace.
- They may appear as if they are coming from a reliable personality within the firm.
Curious about the difference between social engineering and phishing? Read our detailed guide to learn how to protect yourself from these threats.
3. Whaling
Characteristics of Whaling Emails:
- They do not speak about low level issues such as operational or day to day activities.
- It involves its utilization appearing sometimes to be from the top management or the board of directors.
- They may include attachments or links to fake websites.
4. Business Email Compromise (BEC)
Characteristics of BEC Emails:
– They come from what appears to be a legitimate executive email account.
– They include specific instructions about financial or confidential matters.
– Often use urgent language to prompt quick action from employees.
Why Social Engineering is Effective in Email Security Attacks

Social engineering works well because it targets human psychology instead of technology. Hackers understand that people, even with security software, can be predictable. Here are the key reasons why social engineering is effective:
1. Trust
People naturally trust emails that appear to come from familiar organizations or individuals. If an email seems to be from your bank or your boss, you are likely to follow its instructions without questioning it.
2. Fear and Urgency
Social engineering emails create fear or urgency to prompt quick actions. For example, a phishing email might warn, “Your account will be locked in 24 hours.” This urgency leads people to act quickly, without thinking.
3. Curiosity and Greed
Emails offering rewards or unusual information play on curiosity and greed. For instance, an email might claim you’ve won a prize or have a critical update about your tax refund. This can tempt people to click links or download attachments.
4. Poor Security Awareness
Many individuals and businesses underestimate the risks of email security. This lack of awareness makes them more susceptible to social engineering attacks and can lead to costly security breaches.
Want to know how social engineering can compromise your security? Check out our blog to learn how to defend against these cyber threats!
Steps to Protect Against Social Engineering in Email Security

Protecting against social engineering attacks in email requires a mix of technology and awareness. Here are some effective strategies for individuals and organizations:
1. Educate and Train Employees
Training employees to recognize social engineering tactics is one of the best defenses. Regular training sessions, mock phishing exercises, and email security workshops help employees learn how to identify risks and respond properly.
2. Use Multi-Factor Authentication (MFA)
Multi-factor authentication adds an extra layer of protection to email accounts. It requires additional verification, which makes it harder for attackers to gain access. Implementing MFA reduces the likelihood of unauthorized access and protects sensitive information.
3. Verify Requests for Sensitive Information
Always verify requests for sensitive information. If an email seems suspicious, directly contact the sender through another method. Do not use contact information from the email, as it may be fake.
4. Regularly Update Security Software
Keep your email security software updated. Regular updates help protect against the latest threats and ensure you have the best defenses in place.
FAQs
Why is it important to be aware of social engineering?
Being aware of social engineering helps you spot tricks that scammers use. This knowledge protects you from giving away personal information.
Why is email security important in cyberspace?
Email security is vital because many cyber attacks begin with phishing emails. By protecting your email, you keep your valuable data safe from hackers.
What is social engineering in cybersecurity phishing?
In cybersecurity, social engineering phishing tricks people into sharing sensitive information. Scammers use fake emails to manipulate trust and gain access to your data.
What are the four types of social engineering?
The four types of social engineering include phishing, pretexting, baiting, and tailgating. Each type uses unique methods to deceive victims. Understanding these types helps you stay alert and safe.
Final Words
Social engineering is a serious threat to email security. It can lead to significant harm if not properly addressed. Being aware of the different types of social engineering attacks, such as phishing and business email compromise, is crucial in protecting sensitive information.