Phishing is a type of cybercrime. In this scheme, attackers try to deceive people. They aim to get personal information. This includes passwords, credit card details, and identification numbers. This is normally achieved by fake emails, messages, or bogus websites in an attempt to mimic genuine organizations or individuals. The primary motive for phishing is to get to know the personal information of the target or introduce malevolent programming on the target’s machine.
Listen to Our Podcast: Phishing and How to Prevent It
Phishing attacks can take various forms:
1. Email Phishing:
This is the most common type. In this case, the attacks are sent in the form of emails. They seem as if they were sent by well-known organizations. They often ask the recipient to check an updated link download an attachment, and so on.
2. Spear Phishing:
As the name suggests, instead of randomly choosing victims, spear phishing focuses on individuals or firms. Attackers research their targets to learn the kind of messages that have a higher probability of prevailing over the targets.
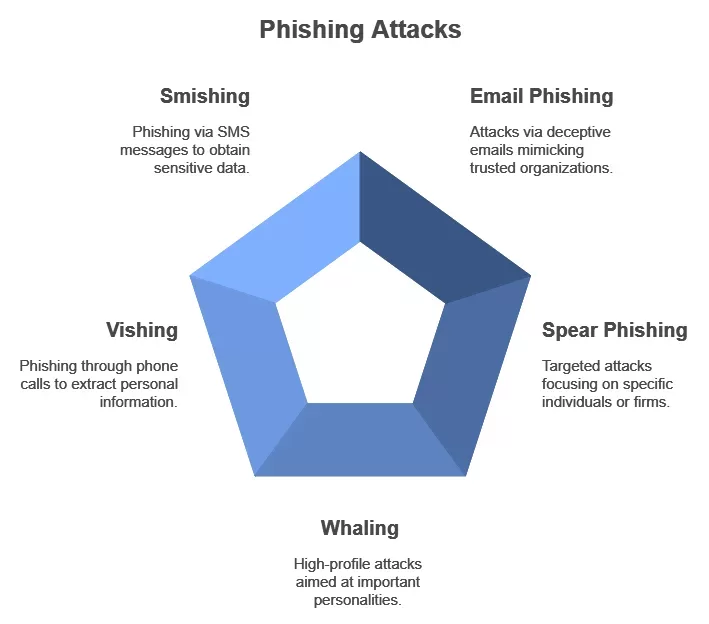
3. Whaling:
This is a type of spear phishing that is designed for important personalities such as officials in a given company or organization.
4. Vishing (Voice Phishing):
Scammers employ a phone call to compel the targeted person to disclose identity details. They can clone the logos of authentic companies and even government agencies.
5. Smishing (SMS Phishing):
This means to send a message to a person in the organization with a link or asking for some information.
According to the results of the experiment, different types of cyber threats such as phishing attacks have been on the rise lately. The APWG further noted that there were in excess of 877,000 phishing cases recorded in the middle of the year 2024, in the second quarter alone. New and improved types of phishing attacks are on the rise, so everyone must learn how best to identify an attack and avoid falling prey to it.
Are you really interested in social engineering? Learn how attackers use psychology to get sensitive information. Check out our blog, What is Social Engineering in Cybersecurity? It will help you recognize these threats and give you tools to fight back effectively!
How Does Phishing Work?

Phishing attacks typically follow a few common steps:
· Preparation:
The method the attacker employs is to gather as much information as possible about the target. This could include email address, names and other information about the individual person.
· Creation of Deceptive Content:
The attacker develops a message that falsely looks like an authentic email or message. This typically involves logos, language, and layouts that are pseudo-realistic, surrogating real organizations.
· Distribution:
The attacker sends out the phishing email or message to a large number of people, hoping that some will fall for the trick.
· Execution:
If a victim clicks a link or downloads an attachment, they might visit a fake website. This site is designed to capture personal information. It can also install malware on the device.
· Data Theft:
Once the attacker has the victim’s information, they can use it for financial gain, identity theft, or other malicious purposes.
What are Common Signs of Phishing?
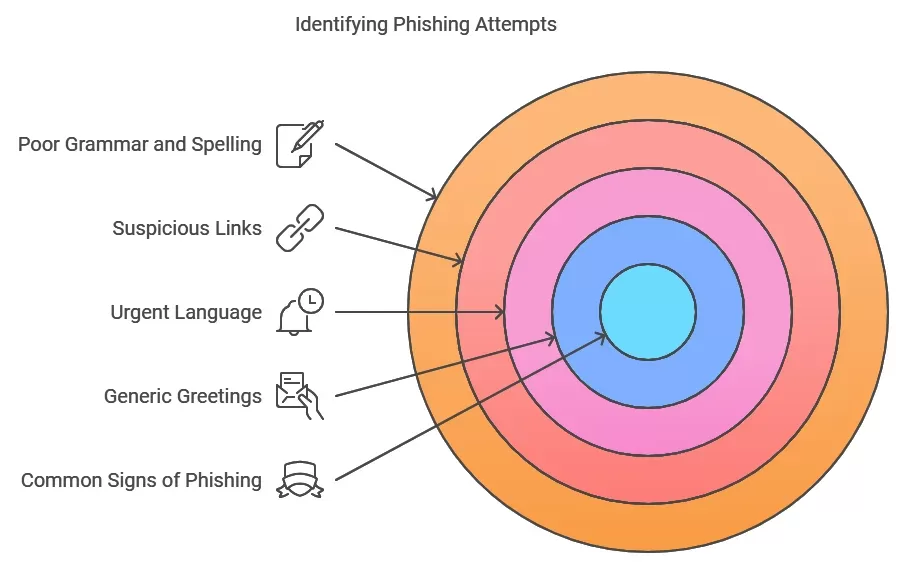
Recognizing phishing attempts can be challenging but knowing what to look for can help:
· Generic Greetings:
Many phishing emails start with “Dear Customer” instead of using your name.
· Urgent Language:
Phishing messages often create a sense of urgency, prompting you to act quickly without thinking.
· Suspicious Links:
Hovering over links in emails can reveal the actual URL. If it looks strange or does not match the supposed sender’s website, it’s likely a phishing attempt.
· Poor Grammar and Spelling:
Many phishing emails contain errors in spelling and grammar.
· Unexpected Attachments:
Be cautious of attachments from unknown senders; they may contain malware.
So, understanding these signs can help you avoid falling victim to phishing scams.
Want to know about social engineering? Learn how cybercriminals trick people to steal sensitive information. Check out our easy guide on What is Social Engineering and How Does It Work? Gain the knowledge to protect your digital life!
Social Engineering and Its Role in Phishing

Phishing is often seen as a part of social engineering. It manipulates people into giving away confidential information. Social engineering takes advantage of human psychology. It creates scenarios that lead victims to share sensitive data.
Cybercriminals use various tactics in social engineering:
Impersonation: Attackers may pose as trusted figures such as colleagues or IT support personnel.
Creating Urgency: They often induce panic or urgency to prompt quick actions from victims.
Exploiting Trust: By using established relationships or authority figures, attackers can manipulate victims into compliance.
However, it’s important to understand social engineering tactics. They are often used with phishing attacks. By recognizing these methods, individuals can better protect themselves. This helps defend against potential threats.
Confused about social engineering and phishing? They have different tactics. Attackers target people in unique ways. Read our guide on Social Engineering vs Phishing to learn more and stay safe from these threats!
How to Prevent Phishing Attacks

Preventing phishing requires awareness and proactive measures. Here are some effective strategies:
1. Be Skeptical of Unsolicited Communications
Always be cautious when receiving unsolicited emails or messages asking for personal information. Legitimate organizations typically do not request sensitive data via email.
2. Verify Sources
If you get a suspicious email from a company, act cautiously. Contact the company directly. Use official contact information from their website. Do not click on links in the email.
3. Use Strong Passwords
Create strong passwords that combine letters, numbers, and symbols. Avoid using easily guessable information like birthdays or names. Change your passwords regularly and consider using a password manager to keep track of them securely.
4. Enable Two-Factor Authentication (2FA)
Two-factor authentication adds security. It requires your password and another piece of information. This could be a code sent to your phone. You need both to access your account.
5. Keep Software Updated
Update your operating system regularly. Keep your software applications up to date. This helps protect against vulnerabilities. Attackers may exploit these weaknesses.
6. Educate Yourself and Others
Stay informed about phishing techniques. Educate those around you. Share knowledge with friends, family, and coworkers. Teach them how to recognize phishing attempts.
7. Use Anti-Phishing Tools
Many email providers offer built-in spam filters that help detect phishing attempts. Additionally, consider using antivirus software that includes anti-phishing features.
Final Words
Finally, as you learned phishing is a serious threat. So, understanding how it works is important. It often involves social engineering. Always be cautious with unsolicited communications. Verify sources before sharing personal information. Use strong passwords and two-factor authentication. Keep your software updated. Educate yourself about potential threats. Utilize available anti-phishing tools.